Hello everyone, we are Aluba Studios, and we are happy to share our game with you: Cyber Manhunt. Yes, this is a cyber manhunt games, combined with a network of violence, big data, loss of privacy and other social problems, to the story of puzzle games.
Cyber Manhunt is a series that is currently running and has 1 seasons (1 episodes). The series first aired on May 27, 2013. Cyber Manhunt is available for streaming on the website, both individual episodes and full seasons. You can also watch Cyber Manhunt on demand atiTunes online. The Cyber Manhunt Cyber Manhunt, also known as Human Flesh Search or Internet Mass Hunting is primarily a Chinese Internet phenomenon of massive searching in which numerous Internet users participate to filter the search results and assists users in clarifying their search request.
Hello everyone, we from Aluba Studios, and we are happy to share our game with you: Cyber Manhunt.
Yes, this is a story-oriented puzzle game related to the cyber manhunt, it combines the social problems such as cyber violence, big data and privacy disclosure.
Many of our story settings refer to real events, you may find something familiar in the design of the game characters. In the game, you may also remember some social events that happened in the real world.
We thought for a long time when determining the theme of the game. Because we are influenced by such excellent independent games as This War of Mine, Papers pleaseand Orwell, we want to make a game that inspires players to think deeply in the game and resonate with reality. Therefore, the work on the game theme has exhausted our soul.
Theme idea
In the 'friendly' communication with the team project meeting, we found that when the Internet continues to penetrate people's lives and accelerate the transmission of information, a negative event can quickly be publicized throughout the Internet.
In this process, the evil will be exposed and punished which make the majority of people feel happy; but some people will suffer malicious insults from the Internet keyboard warrior. When these cyber violences continues to escalate,the results often go beyond the event itself, some people in the incident even choose to end their precious lives when they are overwhelmed.
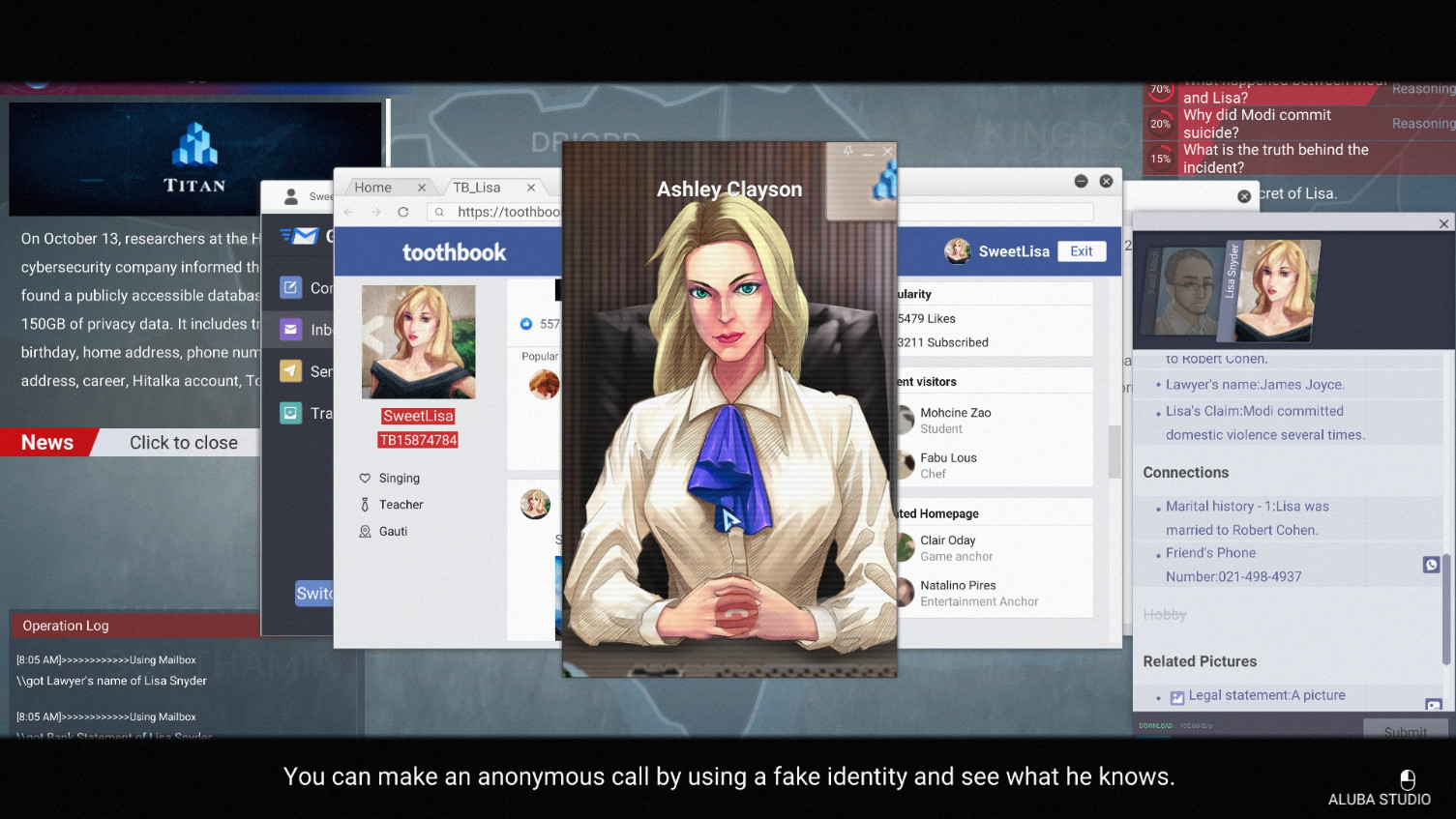
Therefore, we decided to develop such a game related to the theme of 'hacking', 'cyber manhunt' and 'privacy data leakage'. We wang to allow players to act as a hacker who uses social engineering to find out the privacy and secrets of the target (victim). Just like a “god” controls the destiny of others behind somebody back and witnesses their end. We hope players can think in-depth and make their own judgments during the game.

Development progress
After a few months of hard work, we completed part of the game idea:
Implemented some cyber manhunt method and integrated them into our game:
- Web search: The player collects basic information about the target person of the browser search function.
- Database: Use known information to search in the database, filter and get other information about the target person.
- Crack: Generate passwords based on the obtained target person information, and use it to log in the target person's account.(including email, social platforms, chat software, etc.)
- Disguise:To get further information about the target person, contact with the target person is necessary. This requires the player to get the needs and social circles of the target person and choose the suitable disguise.
- Chat spoofing:To get further information about the target person, contact with the target person is necessary. This requires the player to get the needs and social circles of the target person and choose the suitable disguise.
- Picture analysis: Get valuable information and relevant clues from photos and pictures.
- Phishing:Send phishing links to the target person's hardware devices (computer, mobile phone) , and obtain private information.
Of course, more advanced cyber manhunt methods will be unlocked later!
Without any doubt, as a hacker, you need to evade the pursuit of the police, so you should always be careful not to indulge on the Internet and change your IP address in time. In addition to these, a large number of NPCs will be added. Each person has his own personality and story. There is a special connection with the protagonist. Different choices will trigger different endings.
Based on all we mentioned above, let's talk about the difficulties that are still being overcome: the story, this is the most challenging task we feel about. Currently, we just have a story outline, detailed story development and timeline have not been completed, as well as the reversal events. We know that a good main story is very important for this type of game, so this will be our future research and development focus.
Gameplay
In fact, the gameplay is the same as the games I mentioned at the beginning, just click the mouse. (Cross out)
Just kidding, here's the real gameplay (currently):
1. The player is a hacker in the game who accept missions from a reporter and complete social engineering attack tasks.
2. Throughout the process, the players need to use a variety of social engineering attack methods to achieve the mission goal;
3. Each social engineering attack method has corresponding usage conditions. Choosing the correct method will enable the player to get clues;
4. A police officer will always try to trace the player, and the player needs to change the IP address in time;
5. The game will judge the good and evil of the player's behavior. Different judgments will trigger the corresponding stories and events spread out.
Development History
(some characters)
During the preparation of game materials, when we collected news events related to 'Internet violence', 'cyber manhunt' and 'privacy leaks', we found that such cases were really endless. And there are more specialized terms of with cyber manhunt: social engineering. (I will replace cyber manhunt with social engineering later, it seems our team is a bit more professional)
In order to give players a realistic hacking experience, we even established a social engineering group to find some experts in the industry and ask them about social engineering. We even read the book The Art of Deception by the famous hacker Kevin David Mitnick , and saw how the real hacker masterworks . These online and offline learning directly opened the door to a new world for everyone in our team. The disciplines involved social engineering, psychology, micro-expressions, tactics, etc. The rich game content makes us full of confidence in terms of subject and gameplay.
Not just professionals and books, we are also looking for inspiration in some movies. For example, through Who Am I: No System Is Safe, we have seen more artistic and more representative forms of hacking technology. Through Searching we have learned how to create reversals in detail and let the audience / player focus on where we expect them to focus. Every point we learned could polish our game a lot, so we can't wait to use them in our games.
Of course, this is just the second independent game produced by our team, we encountered many problems through the whole development process. For example, we expect to bring the most authentic social engineering experience to players, but real social engineering is very boring. Most of the time, hackers are actually thinking and planning how to achieve the attack which undoubtedly reduces the fun of the game. But if we compromise for the gaming experience, the authenticity of the social engineering attack drops again.
We overturned the designed scheme and interface again and again in order to find the balance point that can not only make the players understand the real social engineering attack process, but also get started easily with exciting gaming experience.
When each game version was released, we always find some things that have not achieved the expected effect. During iteration, the game has been updated 32 times. Of course, this is not the end of the game iteration and we believe that each update brings an improvement to the game. (Thanks to programmers and artists for their tolerance.) In the process, the version number of the game became longer, but the hairline of everyone in the team became higher.
(Overthrow first edition interface)
(Overthrow second edition interface )
(Overthrow third edition interface )
( interface currently in use )
Team introduction
(some characters)
We are a relatively young team. The studio was founded in the first half of 2019 and currently has a total of seven members.
Before the team was formed, we had developed our first game on the Steam platform.
Since it was the first time for us to get involved in an independent game. In fact, it was just an attempt without considering too much, even the theme of the game was decided in a second. (Quite sloppy)
Due to lack of experience, we encountered many problems in the process, but fortunately, many friends of the industry helped us and eventually made the game successfully released.
Cyber Manhunt Game W
In fact, when the game was just launched, we didn't have many expectations, because we knew that our skill level was very limited, but the results were quite satisfactory, and we were lucky to have won a prize by this game in creative game competition.
All these experiences motivated us and let us realized that in the independent game community, whether it is players, developers, or publishers, Everyone has a heart that loves games. Consequently, we decided to sum up the gains and losses from the experiences, and put all our energy into the game cyber manhunt.


Write at the end
Although the development process is difficult, we hope this game will enable the awareness of players that the importance of protecting personal privacy data, the harmfulness of cyber manhunt and the destructive nature of online violence.
Above all, we hope you enjoy the game.
The following is my contact information. If you have any comments or suggestions, you can contact us, and I look forward to communicating with you.
Wechat : jiangxun
Email:alubastudio@163.com
Locating “Save File” may not be easy for some games. Sometimes it can be found in the “AppData” file, sometimes you have to find it through “Regedit”. This guide will help you on how to find “Save File” for Cyber Manhunt.
Save File Location
- Go to “C:/”.
- Find “Users”.
- Click “UserName”.
- Go to “AppData”.
If “AppData” Doesn’t Appear
Here’s how to display hidden files and folders.
Windows 10
- In the search box on the taskbar, type folder, and then select “Show hidden files and folders” from the search results.
- Under Advanced settings, select “Show hidden files, folders, and drives” and then select “OK”.
Windows 8.1
- Swipe in from the right edge of the screen, then select Search (or if you’re using a mouse, point to the upper-right corner of the screen, move the mouse pointer down, and then select Search).
- Type folder in the search box, then select “Folder Options” from the search results.
- Select the “View” tab.
- Under “Advanced settings”, select “Show hidden files, folders, and drives” and then select “OK”.
Windows 7
Download Manhunt Pc
- Select the Start button, then select “Control Panel > Appearance and Personalization”.
- Select “Folder Options”, then select the “View” tab.
- Under “Advanced settings”, select “Show hidden files, folders, and drives” and then select OK.
How to Find Save File?
- Go to “LocalLow”
- Find:
Cyber Manhunt Game Walkthrough Chapter 3
C:UsersusernameAppDataLocalLowALUBA
Cyber Manhunt Game
Similar Posts:
